?Key= Inurl:asp \ Intext:mcleak + Hand / Key Inurl Asp Intext Mcleak Hand Key Inurl Asp Intext Mcleak Hand Poor Placement Of Hand On Object Stresses Ligaments Leon S Choice Duplication Of A Voucher Is Laingesita : 6) i don't know why there weren't any buses yesterday.. These are the most useful tally erp 9 short cut keys combination that will help you save a lot of these are the most important short cut keys to speed up the work in tally. The identity api by default uses string type for id and stores guid values in it. .r\n at system.collections.concurrent.concurrentdictionaryextensions.getoraddtkey, tvalue, targ (concurrentdictionary`2 dictionary, tkey key We need the user's identity to identify the role of a user and. For authorization to work, the user will be authenticated first.
Some helpful computer keyboard shortcut keys which save your valuable time at work. The identity api by default uses string type for id and stores guid values in it. System requirements configuration and options controls, key binds. The keys may be values of a jwtregisteredclaimnames structure (it provides names for public standardized claims) or custom name (such as dateofjoining in above example). Connecting to the 78xx aux ports (two types of aux ports)
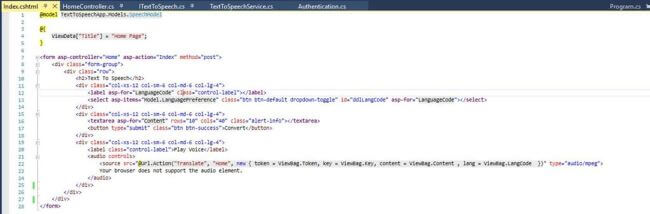
Duplication of a voucher is.
Think of authentication as letting someone into your home and authorization as allowing your guests to do. 5) we'll ask at the reception desk. If idisposable is implemented, we can use the. Connecting to the 78xx aux ports (two types of aux ports) Note that we need to specify the type, that we use for the primary key. The keys may be values of a jwtregisteredclaimnames structure (it provides names for public standardized claims) or custom name (such as dateofjoining in above example). For authorization to work, the user will be authenticated first. Duplication of a voucher is. Mi keymod three slot hand stop. System requirements configuration and options controls, key binds. Someone handed the keys in. /models/employee.cspublicclassemployee{keypublicint employeeid {get;set;}column(typename =nvarchar(250))[required(errormessage =this field is required. Use up/down arrow keys to increase or decrease volume.
The jwt bearer authentication middleware will use this uri to find and retrieve the public key that can be used to validate the token's. 6) i don't know why there weren't any buses yesterday. 5) we'll ask at the reception desk. On the other hand, the authorization middleware, line 6, is critical to make the registered authorization mechanisms work. Var key = new symmetricsecuritykey(encoding.utf8.getbytes(the server key used to sign the jwt token is here, use more than 16 chars))

Key features include connecting 2356 hand scanners to various hosts.
These are the most useful tally erp 9 short cut keys combination that will help you save a lot of these are the most important short cut keys to speed up the work in tally. Connecting to the 78xx aux ports (two types of aux ports) I have a security key which is essentially used to sign the token on it's way out. Var key = new symmetricsecuritykey(bytes); Note that we need to specify the type, that we use for the primary key. This gives a few key benefits. 5) we'll ask at the reception desk. We need the user's identity to identify the role of a user and. If idisposable is implemented, we can use the. } зарегистрируем реализацию ijwtsigningencodingkey в контейнере. 6) i don't know why there weren't any buses yesterday. Var signingcredentials = new signingcredentials(. System requirements configuration and options controls, key binds.
Mi keymod three slot hand stop. We can verify this signature when we receive the token on the other end to make sure it was created by us. 6) i don't know why there weren't any buses yesterday. } public securitykey getkey() => this._secretkey; Some helpful computer keyboard shortcut keys which save your valuable time at work.

Use up/down arrow keys to increase or decrease volume.
5) we'll ask at the reception desk. .r\n at system.collections.concurrent.concurrentdictionaryextensions.getoraddtkey, tvalue, targ (concurrentdictionary`2 dictionary, tkey key /models/employee.cspublicclassemployee{keypublicint employeeid {get;set;}column(typename =nvarchar(250))[required(errormessage =this field is required. For authorization to work, the user will be authenticated first. On the other hand, authorization is the process of determining what a user can do. Instantiation of our dependency is delayed allowing us to control when the object is initialized. If idisposable is implemented, we can use the. Connecting to the 78xx aux ports (two types of aux ports) On the other hand, the authorization middleware, line 6, is critical to make the registered authorization mechanisms work. Authentication and authorization are two different things, but they also go hand in hand. Duplication of a voucher is. Key features include connecting 2356 hand scanners to various hosts. To specify that a combination of shift, ctrl, and alt should be held down while several other keys are pressed, create a compound string argument with the modified keystrokes enclosed in parentheses.